Table of Contents
Generate Root CA certificate
Generate private key
You should enter a password when required.
openssl genrsa -des3 -out ca.key 2048
Output:
Generating RSA private key, 2048 bit long modulus (2 primes) ..............................+++++ ............+++++ e is 65537 (0x010001) Enter pass phrase for ca.key: Verifying - Enter pass phrase for ca.key:
Update the Root CA configuration
Edit the following configuration lines (if needed.)
- root-ca.conf
[ req ] default_bits = 2048 default_keyfile = ca.key distinguished_name = req_distinguished_name x509_extensions = v3_ca string_mask = nombstr req_extensions = v3_req [ req_distinguished_name ] countryName = RO countryName_default = RO countryName_min = 2 countryName_max = 2 stateOrProvinceName = Romania stateOrProvinceName_default = Romania localityName = Bucharest localityName_default = Bucharest 0.organizationName = AX 0.organizationName_default = AX organizationalUnitName = AX Software organizationalUnitName_default = AX Software commonName = AX Root CA commonName_max = 64 emailAddress = admin@ax.com emailAddress_max = 40 [ v3_ca ] basicConstraints = critical,CA:true subjectKeyIdentifier = hash [ v3_req ] nsCertType = objsign,email,server
Generate the final Root CA certificate
openssl req -new -x509 -days 3650 -config root-ca.conf -key ca.key -out ca.crt
Output:
Enter pass phrase for ca.key: You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- RO [RO]: Romania [Romania]: Bucharest [Bucharest]: AX [AX]: AX Software [AX Software]: AX Root CA []: admin@ax.com []:
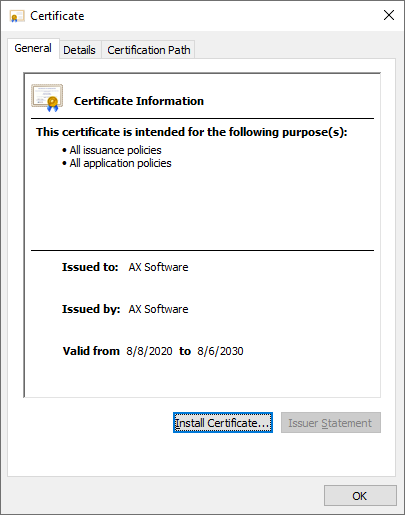
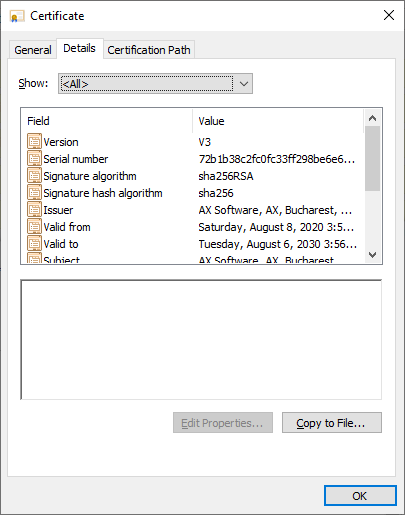
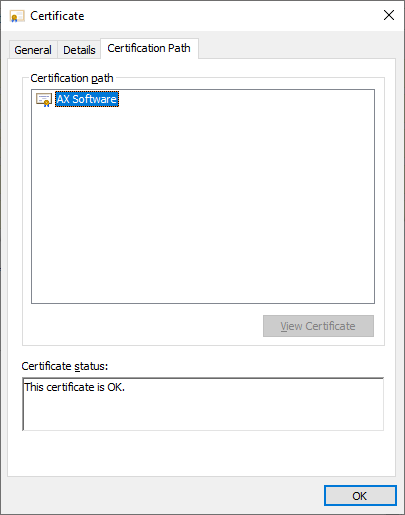
ca.crt images:
Generate a certificate signed by the previously created Root CA
Generate private key and certificate request
This will generate the private key - int1.key and the certificate request - int1.csr. Leave empty the challenge password.
openssl req -new -newkey rsa:2048 -nodes -keyout int1.key -out int1.csr
Output:
Generating a RSA private key ..........+++++ .........+++++ writing new private key to 'int1.key' ----- You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [AU]:RO State or Province Name (full name) [Some-State]:Romania Locality Name (eg, city) []:Bucharest Organization Name (eg, company) [Internet Widgits Pty Ltd]:AX Organizational Unit Name (eg, section) []:AX Software Common Name (e.g. server FQDN or YOUR name) []:item-ax32034 Email Address []:item@ax.com Please enter the following 'extra' attributes to be sent with your certificate request A challenge password []: An optional company name []:
Create extension file (ssl.conf)
- ssl.conf
[ req ] default_bits = 2048 distinguished_name = req_distinguished_name req_extensions = req_ext [ req_distinguished_name ] countryName = RO countryName_default = RO stateOrProvinceName = Romania stateOrProvinceName_default = Romania localityName = Bucharest localityName_default = Bucharest organizationName = AX organizationName_default = AX commonName = item-ax32034 commonName_max = 64 commonName_default = localhost [ req_ext ] subjectAltName = @alt_names [alt_names] DNS.1 = item-ax DNS.2 = item-ax.com
Generate the actual certificate (int1.crt) singed by the Root CA (ca.crt)
openssl x509 -req -in int1.csr -CA ca.crt -CAkey ca.key -CAcreateserial -out int1.crt -days 1000 -sha256 -extensions req_ext -extfile ssl.conf
Output:
Signature ok subject=C = RO, ST = Romania, L = Bucharest, O = AX, OU = AX Software, CN = item-ax, emailAddress = item@ax.com Getting CA Private Key Enter pass phrase for ca.key:
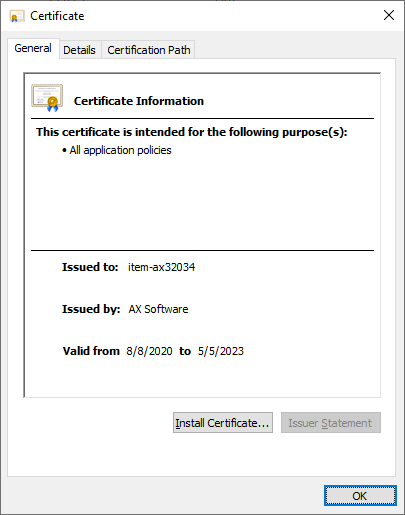
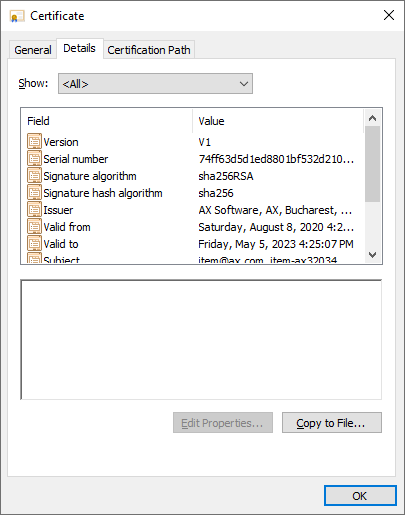
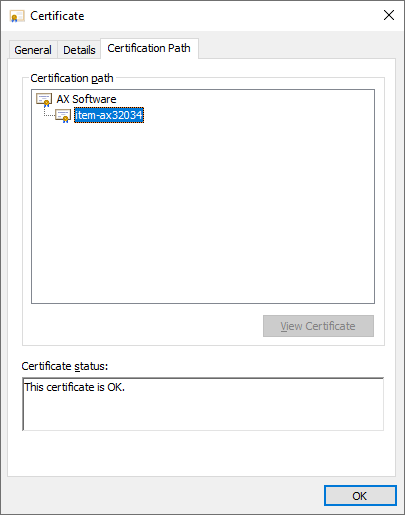
int1.crt images:
Generate an intermediate CA
Edit the following configuration lines (if needed.)
- int1.conf
[ ca ] default_ca = default_CA [ default_CA ] dir = . certs = . new_certs_dir = ca.db.certs database = ca.db.index serial = ca.db.serial RANDFILE = random-bits certificate = ca.crt private_key = ca.key default_days = 1000 default_crl_days = 30 default_md = sha256 preserve = no x509_extensions = server_cert policy = policy_anything [ policy_anything ] countryName = optional stateOrProvinceName = optional localityName = optional organizationName = optional organizationalUnitName = optional commonName = supplied emailAddress = optional [ server_cert ] #subjectKeyIdentifier = hash authorityKeyIdentifier = keyid:always extendedKeyUsage = serverAuth,clientAuth,msSGC,nsSGC basicConstraints = critical,CA:true
In the same folder create the directory ca.db.certs, the file ca.db.serial with the content 01 and the empty file ca.db.index:
mkdir ca.db.certs echo 01 > ca.db.serial type NUL > ca.db.index
Generate the private key and csr:
openssl req -new -newkey rsa:2048 -nodes -keyout int1.key -out int1.csr
Output:
Generating a RSA private key .............................+++++ ............................................+++++ writing new private key to 'int1.key' ----- You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [AU]:RO State or Province Name (full name) [Some-State]:Romania Locality Name (eg, city) []:Bucharest Organization Name (eg, company) [Internet Widgits Pty Ltd]:AX Organizational Unit Name (eg, section) []:AX INT1 CA Common Name (e.g. server FQDN or YOUR name) []:item-ax32034-INT1 Email Address []:int1@ax.com Please enter the following 'extra' attributes to be sent with your certificate request A challenge password []: An optional company name []:
Generate the actual intermediate CA:
openssl ca -config int1.conf -out int1.crt -infiles int1.csr
Output:
Using configuration from int1.conf Enter pass phrase for ca.key: Check that the request matches the signature Signature ok The Subject's Distinguished Name is as follows countryName :PRINTABLE:'RO' stateOrProvinceName :ASN.1 12:'Romania' localityName :ASN.1 12:'Bucharest' organizationName :ASN.1 12:'AX' organizationalUnitName:ASN.1 12:'AX Software' commonName :ASN.1 12:'AX INT1 CA' emailAddress :IA5STRING:'int1@ax.com' Certificate is to be certified until May 5 14:59:03 2023 GMT (1000 days) Sign the certificate? [y/n]:y 1 out of 1 certificate requests certified, commit? [y/n]y Write out database with 1 new entries Data Base Updated
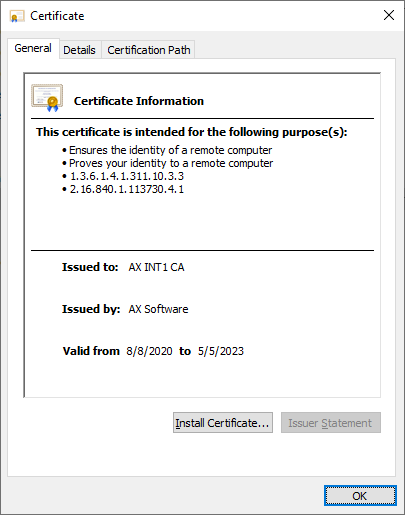
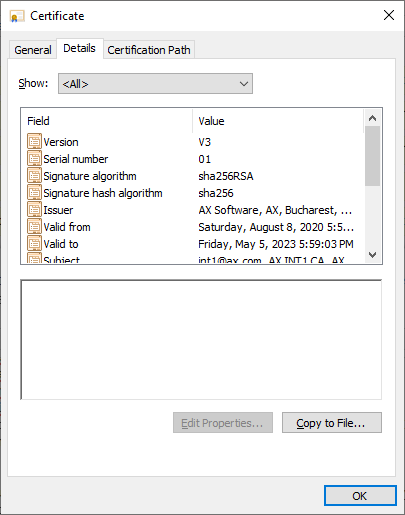
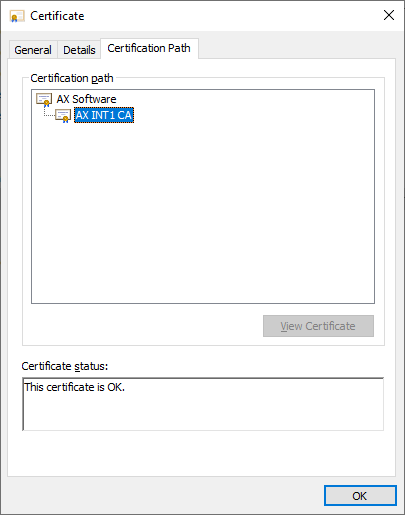
int1.crt images:
Generate another intermediate CA
Repeat the steps for the above configuration, but change the config file as:
- int2.conf
[ ca ] default_ca = default_CA [ default_CA ] dir = . certs = . new_certs_dir = ca.db.certs database = ca.db.index serial = ca.db.serial RANDFILE = random-bits certificate = int1.crt private_key = int1.key default_days = 500 default_crl_days = 30 default_md = sha256 preserve = no x509_extensions = server_cert policy = policy_anything [ policy_anything ] countryName = optional stateOrProvinceName = optional localityName = optional organizationName = optional organizationalUnitName = optional commonName = supplied emailAddress = optional [ server_cert ] #subjectKeyIdentifier = hash authorityKeyIdentifier = keyid extendedKeyUsage = serverAuth,clientAuth,msSGC,nsSGC basicConstraints = critical,CA:true
Then generate the private key and csr:
openssl req -new -newkey rsa:2048 -nodes -keyout int2.key -out int2.csr
Finally generate the certificate:
openssl ca -config int2.conf -out int2.crt -infiles int2.csr
Output:
Using configuration from int2.conf Check that the request matches the signature Signature ok The Subject's Distinguished Name is as follows countryName :PRINTABLE:'RO' stateOrProvinceName :ASN.1 12:'Romania' localityName :ASN.1 12:'Bucharest' organizationName :ASN.1 12:'AX' organizationalUnitName:ASN.1 12:'AX INT2 CA' commonName :ASN.1 12:'item-ax32034-INT2' emailAddress :IA5STRING:'int2@ax.com' Certificate is to be certified until Dec 21 15:39:26 2021 GMT (500 days) Sign the certificate? [y/n]:y 1 out of 1 certificate requests certified, commit? [y/n]y Write out database with 1 new entries Data Base Updated
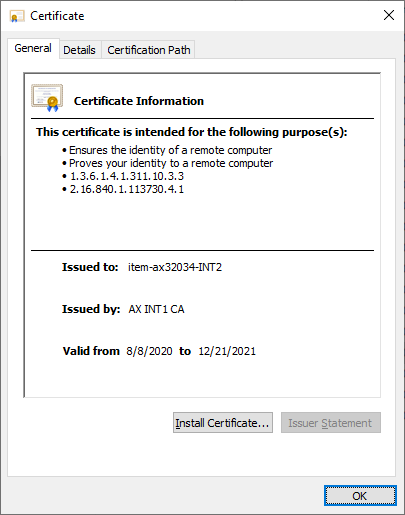
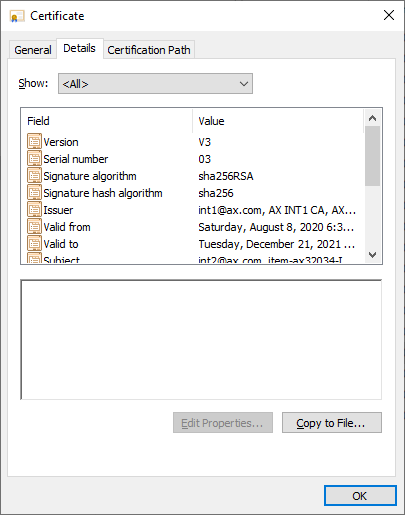
Final CA certificate with 2 intermediate CA - int2.crt images: